Install SSL Certificate WordPress | How to Install SSL on WordPress Website (FREE)
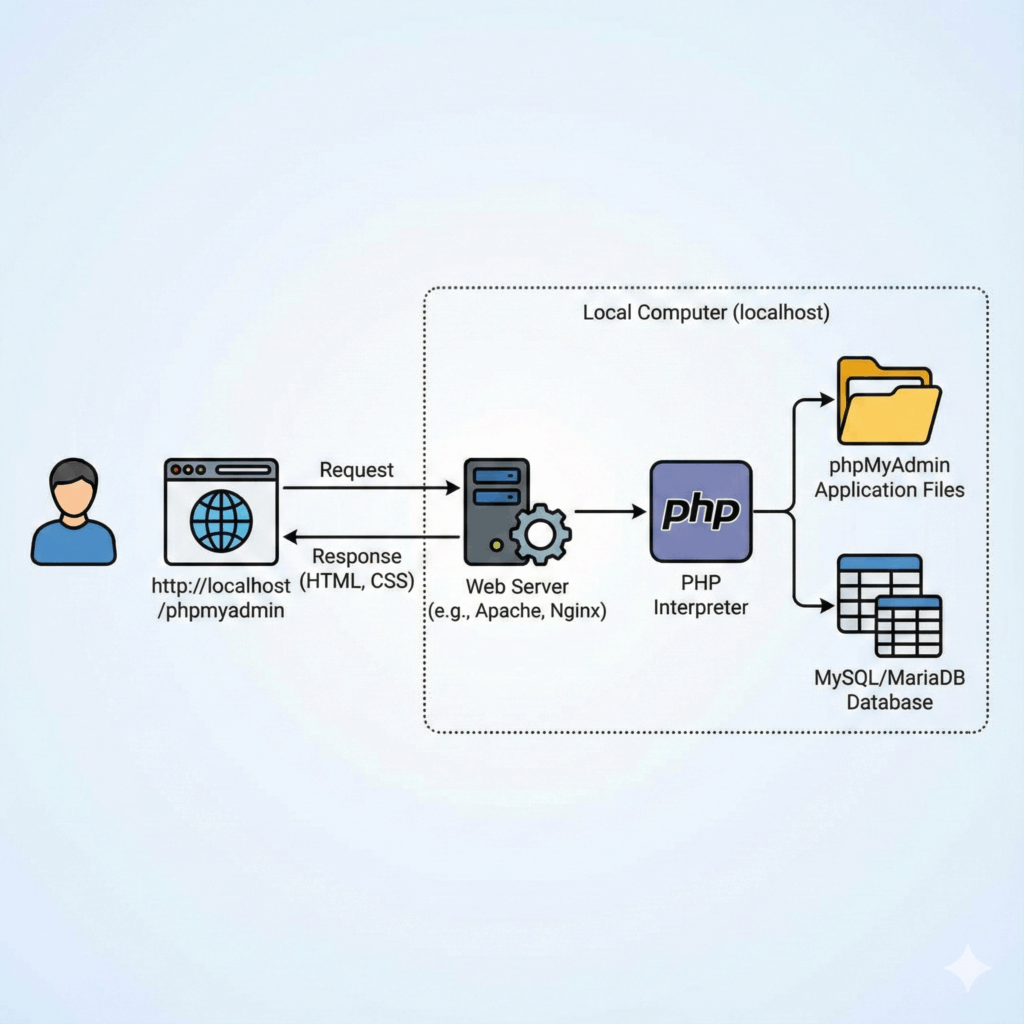
How to enable SSL (https protocol) with Xampp in a local PHP project
How to get an SSL certificate for localhost?
To get an SSL certificate for localhost, follow these steps:
1. Install OpenSSL: First, you need to have OpenSSL installed on your computer. OpenSSL allows you to generate SSL certificates. It usually comes pre-installed on macOS and Linux. If you’re using Windows, download the installer from the official OpenSSL website and install it.
2. Create a private key and a Certificate Signing Request (CSR): OpenSSL generates a private key and CSR that you’ll use to request an SSL certificate. Open your terminal or command prompt and run the following command:
“`
openssl req -newkey rsa:2048 -nodes -keyout localhost.key -out localhost.csr
“`
This command creates a 2048-bit RSA private key named “localhost.key” and a CSR named “localhost.csr”.
3. Generate a self-signed SSL certificate: Since you’re creating an SSL certificate for localhost, you can generate a self-signed certificate. Run the following command:
“`
openssl x509 -req -days 365 -in localhost.csr -signkey localhost.key -out localhost.crt
“`
This command creates a self-signed certificate named “localhost.crt” that is valid for 365 days.
4. Configure your web server: Now that you have the private key and SSL certificate, you need to configure your web server to use them. The configuration process will vary depending on the web server you are using. For example, if you’re using a Node.js Express server, you can use the following code snippet:
“`javascript
const https = require(‘https’);
const fs = require(‘fs’);
const express = require(‘express’);
const app = express();
// Your application logic here
app.get(‘/’, (req, res) => {
res.send(‘Hello world with SSL!’);
});
const privateKey = fs.readFileSync(‘localhost.key’, ‘utf8’);
const certificate = fs.readFileSync(‘localhost.crt’, ‘utf8’);
const ca = fs.readFileSync(‘CA.crt’, ‘utf8’);
const credentials = {
key: privateKey,
cert: certificate,
ca: ca
};
const server = https.createServer(credentials, app);
server.listen(3000, () => {
console.log(‘Server running on https://localhost:3000’);
});
“`
Check the documentation for your specific web server to see how to configure SSL.
5. Trust the self-signed certificate (optional): Since the SSL certificate is self-signed, your browser will show a security warning when you access localhost. To avoid this, you can add the certificate to your system or browser’s trusted root certification authorities. The process differs depending on your operating system and browser.
Once these steps are done, you will be able to access your localhost application over HTTPS using an SSL certificate.
Can localhost have an SSL certificate?
Yes, localhost can have an SSL certificate. To enable SSL on localhost, you will need to generate a self-signed SSL certificate, which is used primarily for development and testing purposes. However, please note that modern browsers still display a warning for self-signed certificates, as they are not issued by a trusted certificate authority (CA).
To create a self-signed SSL certificate, follow these steps:
1. Install OpenSSL, if it’s not already installed, to manage the certificates.
2. Run a command in your terminal or command prompt to generate a new private key and certificate signing request (CSR).
3. Use the CSR to create a self-signed SSL certificate with a specified expiration date.
4. Configure your local server, such as Apache or Nginx, to use the generated SSL certificate.
Once you’ve completed these steps, you can access your local development site using HTTPS. However, always remember that self-signed SSL certificates should not be used in a production environment.
How to create SSL certificate in Windows for localhost?
To create an SSL certificate in Windows for localhost, follow these steps:
1. Install OpenSSL: First, you need to download and install the OpenSSL toolkit for Windows. You can download the binaries from [this link](https://slproweb.com/products/Win32OpenSSL.html). Make sure to choose the appropriate version for your system (32-bit or 64-bit).
2. Create a configuration file: Open your favorite text editor and create a configuration file named `localhost.cnf` with the following content:
“`
[req]
distinguished_name = req_distinguished_name
x509_extensions = v3_req
prompt = no
[req_distinguished_name]
CN = localhost
[v3_req]
subjectAltName = @alt_names
[alt_names]
DNS.1 = localhost
IP.1 = 127.0.0.1
IP.2 = ::1
“`
3. Generate the SSL certificate and private key: Open the command prompt as an administrator and navigate to the OpenSSL binary directory (e.g., C:Program FilesOpenSSL-Win64bin). Then, execute the following command, replacing `path/to/localhost.cnf` with the actual path to your `localhost.cnf` file created in step 2:
“`
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout localhost.key -out localhost.crt -config “path/to/localhost.cnf”
“`
4. Install the SSL certificate: Double-click on the `localhost.crt` file to open it with the Windows certificate manager. Click “Install Certificate,” select “Local Machine,” and click “Next.” Choose “Place all certificates in the following store” and click “Browse.” Select “Trusted Root Certification Authorities” and click “OK.” Click “Next” and then “Finish.” A warning will appear, click “Yes” to install the certificate.
5. Configure your development server: To use the generated SSL certificate and private key, you need to configure your development server (e.g., IIS, Apache, or Node.js) to use `localhost.crt` and `localhost.key`. The configuration process may vary depending on the server software you are using.
Once you have completed these steps, your localhost should now be accessible via HTTPS with a valid SSL certificate. Make sure to restart your development server after making any configuration changes.
How to install SSL certificate on localhost IIS?
To install an SSL certificate on your IIS localhost, follow these steps:
1. Create a self-signed certificate: Since you are setting up SSL for a localhost, you’ll need to create a self-signed certificate. Open the IIS Manager by clicking Start, searching for “IIS Manager,” and opening it.
2. In the IIS Manager, click on your local server name in the left pane, then navigate to the “Server Certificates” section by double-clicking the icon in the middle pane.
3. On the right side, click on “Create Self-Signed Certificate.” Enter a friendly name for the certificate and choose “Personal” as the certificate store. Click OK.
4. Assign the SSL certificate to your site: Now that you have created a self-signed certificate, you need to assign it to your localhost site.
5. In the IIS Manager, expand your local server name, then click on “Sites” and select your localhost site.
6. On the right side, click on “Bindings.” A new window will open. Click “Add” to create a new binding.
7. In the Add Site Binding window, set the following options:
– Type: Choose “https”
– IP address: Select “All Unassigned” or the IP address of your localhost
– Port: Set to “443” (default HTTPS port)
– SSL certificate: Choose the self-signed certificate you created earlier
8. Click OK to add the new HTTPS binding.
Now your IIS localhost site is secured with an SSL certificate. Keep in mind that since this is a self-signed certificate, web browsers will show warnings when accessing the site via HTTPS. This is normal, as the certificate is not signed by a trusted authority. However, the connection itself will still be encrypted.
How can I generate and install a self-signed SSL certificate for my localhost environment?
To generate and install a self-signed SSL certificate for your localhost environment, follow these steps:
1. Install OpenSSL: Make sure you have OpenSSL installed on your system. If not, you can download it from the official website: https://www.openssl.org/source/.
2. Create a new directory: Create a new directory where you will store your private key and certificate. For example, you can create a directory named `ssl` in your project folder.
3. Generate a private key: Open a terminal/command prompt and navigate to the directory you just created. Run the following command to generate a private key:
“`
openssl genrsa -out private.key 2048
“`
4. Create a Certificate Signing Request (CSR): Run the following command to create a CSR using the private key:
“`
openssl req -new -key private.key -out server.csr
“`
Fill in the required information. For the common name, use ‘localhost’ if you want this certificate to be valid for your local environment.
5. Generate the self-signed SSL certificate: Run the following command to generate the SSL certificate:
“`
openssl x509 -req -days 365 -in server.csr -signkey private.key -out server.crt
“`
This will create a certificate named `server.crt` that is valid for 365 days.
6. Install the certificate in your web server: Depending on your web server, such as Apache, Nginx, or Node.js, you will need to configure your server to use the private key and SSL certificate.
For example, in an Apache configuration file, add the following lines inside the appropriate VirtualHost block:
“`
SSLEngine on
SSLCertificateFile /path/to/your/server.crt
SSLCertificateKeyFile /path/to/your/private.key
“`
For Nginx, add these lines inside the server block:
“`
ssl_certificate /path/to/your/server.crt;
ssl_certificate_key /path/to/your/private.key;
“`
For a Node.js server using Express, update your app configuration like this:
“`javascript
const fs = require(‘fs’);
const https = require(‘https’);
const express = require(‘express’);
const app = express();
const privateKey = fs.readFileSync(‘/path/to/your/private.key’, ‘utf8’);
const certificate = fs.readFileSync(‘/path/to/your/server.crt’, ‘utf8’);
const sslOptions = { key: privateKey, cert: certificate };
https.createServer(sslOptions, app).listen(3000, () => {
console.log(‘Server running at https://localhost:3000/’);
});
“`
7. Trust the certificate on your system (optional): Since this is a self-signed certificate, browsers will show a security warning. To avoid this, you can add the certificate to your operating system’s trusted root certificates store.
Keep in mind that self-signed certificates should only be used for development and testing purposes, not in production environments. Use a valid SSL certificate provided by a Certificate Authority (CA) for production environments.
What are the steps to configure an SSL certificate for a web server running on localhost?
To configure an SSL certificate for a web server running on localhost, follow these steps:
1. Install OpenSSL: First, ensure that you have OpenSSL installed on your system. If not, download and install it from the official website (https://www.openssl.org/).
2. Create a private key and a Certificate Signing Request (CSR): Open the command prompt or terminal and navigate to the directory where you want to store your private key and CSR. Run the following command to generate a key and a CSR:
“`
openssl req -new -newkey rsa:2048 -nodes -keyout server.key -out server.csr
“`
This creates a 2048-bit RSA private key (server.key) and a CSR (server.csr) in the specified directory.
3. Self-sign the CSR: Since you are configuring the SSL certificate for localhost, you will need to self-sign the CSR. Run the following command:
“`
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
“`
This generates a self-signed SSL certificate (server.crt) that is valid for 365 days.
4. Configure your web server: Now that you have your SSL certificate and private key, you need to configure your web server to use these files for HTTPS connections. The specific process depends on the web server software you are using (e.g., Apache, Nginx, IIS).
For example, in Apache, edit your VirtualHost configuration to include the following lines:
“`
SSLEngine on
SSLCertificateFile “/path/to/server.crt”
SSLCertificateKeyFile “/path/to/server.key”
“`
In Nginx, add these lines to the server block in your configuration file:
“`
ssl on;
ssl_certificate /path/to/server.crt;
ssl_certificate_key /path/to/server.key;
“`
5. Restart the web server: After updating the configuration, restart your web server to apply the changes.
6. Trust the self-signed certificate: Since you are using a self-signed certificate, you will need to add it to your browser’s trusted certificates list, or you’ll receive warnings when visiting your localhost over HTTPS.
Your web server running on localhost should now be configured to use SSL for secure connections.
Are there any security concerns when using a self-signed SSL certificate on localhost, and how can they be mitigated?
There are some security concerns when using a self-signed SSL certificate on localhost. The main concerns include:
1. Lack of trust by default: Web browsers do not trust self-signed certificates by default, meaning users would receive a security warning. This could cause confusion and impact the user experience.
2. Vulnerability to man-in-the-middle (MITM) attacks: Without a trusted Certificate Authority (CA) to validate the legitimacy of your SSL certificate, attackers may generate their own certificates to impersonate your website, leading to possible MITM attacks.
To mitigate these concerns, you can:
1. Use a local development environment: Restrict the use of self-signed certificates to the local development environment, ensuring they are not used in production environments where major security concerns may arise.
2. Obtain a trusted certificate for production: For production environments, obtain an SSL certificate from a trusted CA, such as Let’s Encrypt, which offers free SSL certificates.
3. Add the self-signed certificate to your trusted store: On your localhost machine, add your self-signed certificate to the trust store manually. This will prevent browsers from showing security warnings related to the certificate. However, this should not be done on public-facing websites, as it would not be feasible to have all users manually add your certificate to their trust store.
4. Keep software updated: Regularly update your web server, operating system, and browser to ensure any security vulnerabilities are addressed.