Unraveling the Intricacies of Localhost/Phishing: Your Ultimate Guide
Picture this: you’ve just stumbled upon an ingenious phishing technique that exploits a common aspect of server configuration, and it seems like all your doubts about localhost and phishing will finally be put to rest. But before we delve into the nitty-gritty of this devilishly clever method, let’s make sure we’ve covered all the essentials.
I promise, by the end of this article, you’ll not only understand the fundamentals of localhost and phishing but also be able to protect yourself from this potent cyber threat. Ready? Let’s jump right in.
# H2: The Basics of Localhost
First things first, let’s talk about localhost. Localhost is an IPv4 loopback address (127.0.0.1) or IPv6 address (::1) that points back to the local machine being used by your web server or application. It’s a convenient way for developers to test their projects on their local machines without the need for external connectivity.
Now, you might be wondering how does localhost connect with phishing attacks? Patience, my friend. We’ll get there soon. But before that, let’s zoom in on phishing.
# H2: Phishing 101
Phishing is a type of cyberattack where cybercriminals attempt to trick victims into revealing sensitive information, such as login credentials or financial data, by disguising themselves as a trusted entity. One of the most common methods of phishing involves sending seemingly legitimate emails that contain malicious links or attachments.
So, what happens when we combine localhost and phishing together? Buckle up, because this is where things get interesting.
# H2: Localhost in the Realm of Phishing
As we know, phishers are constantly searching for novel ways to make their malicious content appear more trustworthy. One such approach involves exploiting the concept of localhost to create a false sense of security for the victims. This can be achieved through several techniques, some of which we will discuss in this section.
H3: Localhost URL Manipulation
This method involves the attackers manipulating the target’s browser or software to redirect them to a malicious website hosted on their local machine. The goal is to create a false impression that they’re visiting a legitimate website since the URL starts with “localhost” or “127.0.0.1”.
To achieve this, the phishers create a copy of the genuine website and install it on the victim’s local machine via malicious attachments or links. When the victim opens the attachment or clicks on the link, they might notice the familiar “localhost” address and fall into the trap of entering their sensitive information.
H3: Utilizing Localhost Addresses in Spear Phishing Attacks
In spear-phishing attacks, cybercriminals target specific individuals or organizations. One technique includes utilizing localhost addresses to host malicious content instead of using external servers. This can make it significantly harder for security systems to detect the attack, as the content is hosted locally rather than a suspicious external domain.
H3: Exploiting Incorrect Server Configurations
Sometimes, web developers mistakenly leave their server configurations open, allowing attackers to exploit these vulnerabilities for localhost phishing attacks. In such cases, the attacker gains access to the target’s web server and manipulates the configuration files to redirect users to a localhost phishing page.
# H2: Protecting Yourself from Localhost/Phishing Attacks
By now, you should have a clear understanding of how localhost and phishing can intersect to create a potent cybersecurity threat. But fear not, as there are several ways to safeguard yourself and your organization from such attacks.
H3: Regularly Update Your Software
Ensure that your operating system, web browser, plugins, and all other software are up-to-date. Cybercriminals often exploit vulnerabilities in outdated software to launch their attacks.
H3: Implement Robust Security Measures
Deploy robust security tools, such as firewalls, intrusion detection systems, and anti-phishing software, to detect and prevent potential phishing attacks. Additionally, train your staff members to identify phishing emails and exercise caution when opening attachments or clicking on links.
H3: Configure Your Web Server Securely
Web developers must ensure that their web server configurations are secure and up-to-date. Regularly reviewing and testing the security of your server can help prevent attackers from exploiting vulnerabilities for localhost phishing attacks.
# H2: Wrapping Up
So, there you have it – the full rundown on how localhost and phishing can converge to create a powerful cyberattack, and more importantly, how to protect yourself from falling victim to these cunning techniques. As promised, you’re now equipped with the knowledge to tackle this threat head-on.
Remember, the world of cybersecurity is ever-evolving, so don’t let your guard down. Stay vigilant, stay informed, and most importantly, stay one step ahead of those cybercriminals lurking in the shadows.
SQL Injections are scary!! (hacking tutorial for beginners)
How to Spot Any Spoofed & Fake Email (Ultimate Guide)
What are the common indicators of phishing attempts on a localhost environment?
In a localhost environment, common indicators of phishing attempts include:
1. Unexpected or unsolicited emails: Be cautious of unexpected emails or messages from unknown sources, especially if they contain attachments or links.
2. Generic greetings and incorrect grammar: Phishing emails often have generic greetings and/or a lack of personalization. Additionally, they may contain spelling and grammar errors.
3. Urgent requests for action: Phishers often create a sense of urgency in their messages, pressuring the recipient to act quickly without thinking.
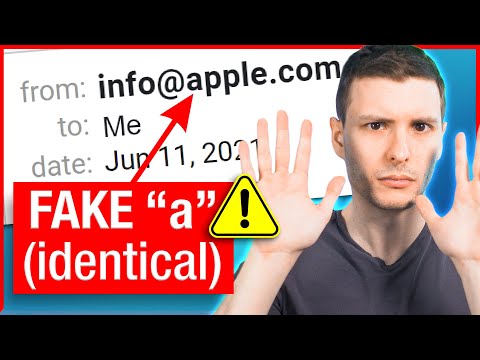
4. Fake sender addresses: Check the sender’s email address closely. Phishers may use fake email addresses that appear similar to legitimate ones.
5. Spoofed websites: Phishers often create fake websites that mimic the look and feel of legitimate ones to trick victims into providing sensitive information.
6. Unsecure connections: URLs starting with “http://” instead of “https://” indicate that the connection is not secure, which could be a sign of a phishing attempt.
7. Unusual file attachments or download requests: Be cautious of downloading files or opening attachments from untrusted sources as they may contain malware.
8. Requests for sensitive information: Legitimate organizations typically do not request sensitive information, such as passwords or financial details, through email.
To protect yourself against phishing attempts on a localhost environment, always verify the source of any suspicious communications, do not click on unknown links or open unexpected attachments, and use strong and unique passwords for your accounts.
How can one effectively protect their localhost server from phishing attacks?
To effectively protect your localhost server from phishing attacks, follow these crucial steps:
1. Keep software up-to-date: Regularly update all software running on your localhost server, including operating systems, web servers, plugins, and any other tools. This ensures that you have the latest security patches to minimize vulnerabilities.
2. Use strong authentication methods: Implement strong authentication techniques, such as two-factor authentication (2FA) or multi-factor authentication (MFA), to ensure that only authorized users can access your localhost server.
3. Install a web application firewall (WAF): A WAF can protect your server by filtering out malicious traffic and analyzing requests sent to the server. This helps prevent common attacks like SQL injection, cross-site scripting, and other web-based vulnerabilities.
4. Encrypt data in transit: Use encryption protocols like SSL/TLS to encrypt data transmitted between the client and the localhost server. This ensures that any information intercepted during transmission remains unreadable.
5. Limit user privileges: Restrict user access to the localhost server to only those who need it, and assign the minimum necessary permissions to each user. This helps reduce the risk of unauthorized access and potential phishing incidents.
6. Regularly monitor and audit: Continuously monitor and analyze logs to detect suspicious activity or unauthorized access attempts. Conduct regular security audits to identify any weaknesses or vulnerabilities in your server setup.
7. Educate users: Train users on the risks of phishing attacks and educate them on how to recognize phishing attempts. Encourage them to report any suspicious activity to the appropriate team for investigation.
8. Implement a solid backup strategy: Regularly back up your localhost server, including databases and important files, to quickly restore your server in case of an attack or data loss.
By following these best practices, you can significantly reduce the likelihood of phishing attacks on your localhost server and better protect your data and applications.
What are the essential steps to take in case a localhost/phishing incident is detected?
Upon detecting a localhost/phishing incident, it is crucial to act promptly and efficiently to minimize damage. Here are the essential steps to follow:
1. Identify the source: Determine where the phishing attack originated or which localhost system is compromised.
2. Isolate the affected system(s): Disconnect the affected device(s) from the network to prevent further spread of the attack.
3. Update security software: Ensure that all security software, including antivirus and firewalls, are up-to-date on all devices connected to your localhost.
4. Change passwords: Change all potentially compromised passwords (including email, bank accounts, and other sensitive data) immediately.
5. Report the incident: Inform the appropriate authorities, such as law enforcement or an IT security team, about the phishing attack.
6. Backup data: Regularly back up all essential data on localhost in case an attack compromises or destroys it.
7. Educate users: Provide training on phishing and related security threats to all users who have access to your localhost environment.
8. Conduct regular security audits: Perform security assessments regularly to identify and address vulnerabilities in your localhost setup.
9. Implement multi-factor authentication (MFA): Enable MFA for critical applications and services to add an extra layer of security.
10. Monitor for suspicious activity: Continuously monitor your localhost for any unusual activities or unauthorized access attempts.