Introduction
Have you ever found yourself tangled in the web of protocols, trying to figure out the best way to communicate securely with a remote server? You are not alone. This article sets out to clarify one of the most common questions among programmers and system administrators – what is the difference between SSH and HTTP? As an experienced programmer or server administrator, understanding these differences is crucial for making informed decisions on which protocol to choose.
By the end of this article, you will not only be able to differentiate between these two protocols, but also determine when to use each of them, ensuring that your connections are secure and efficient. We’ll be providing real-life examples and discussing various scenarios to make it easier to grasp these concepts.
SSH: A Brief Overview
SSH, or Secure Shell, is a cryptographic network protocol that provides secure access to remote servers and computers through an encrypted tunnel. It enables users to execute commands, manage files, and run applications on a remote machine. SSH is widely used by programmers, developers, and system administrators for secure remote access and control.
Key Features of SSH
– Strong encryption and authentication: SSH uses various encryption algorithms to protect the data transmitted between the client and the server.
– Port forwarding: SSH can securely forward traffic from one port to another, enabling secure tunneling of other protocols.
– Public key authentication: SSH supports public key authentication, which eliminates the need to share passwords with remote systems.
HTTP: A General Overview
HTTP, or Hypertext Transfer Protocol, is a request-response protocol that enables communication between clients (web browsers) and servers (websites). When you enter a URL in your browser, an HTTP request is sent to the server, which then sends the requested data back to the client in the form of an HTTP response. HTTP is the foundation of any data exchange on the World Wide Web, and its primary purpose is to transmit and receive data, such as web pages, images, and multimedia content.
Key Features of HTTP
– Stateless protocol: Each HTTP request and response is independent of the others, which means no context or information is stored between transactions.
– Cacheable: HTTP responses can be cached, reducing server load and improving the performance of websites.
– Extensible: HTTP can be extended with additional methods, headers, and status codes to support new functionality and application-specific requirements.
Difference Between SSH and HTTP: A Comparative Analysis
Now that we have a general understanding of each protocol, let’s dive into the key differences between SSH and HTTP.
1. Communication Model
The most significant difference between SSH and HTTP is their communication models – SSH is connection-oriented, while HTTP is stateless. In an SSH connection, a persistent encrypted tunnel is established between the client and the server. This tunnel remains open throughout the duration of the session, allowing for secure and ongoing communication between the two parties.
On the other hand, HTTP operates on a request-response model. Each request and response pair is treated independently, without retaining any information about previous transactions.
2. Security
Another major difference lies in the level of security provided by the protocols. SSH is designed with security in mind and uses strong encryption algorithms, public-key authentication, and host verification to guard against different threats like eavesdropping, man-in-the-middle attacks, and impersonation.
HTTP, in its basic form, is not secure and transmits data in plaintext. However, it can be secured when used with SSL/TLS, giving rise to the HTTPS (Secure HTTP) variant.
3. Usage Scenarios
SSH is predominantly used for remote administration, executing commands, managing files, and running applications on remote systems securely. It is widely employed by developers, programmers, and system administrators for various tasks such as server maintenance, application deployment, and debugging.
HTTP, due to its stateless nature, is more commonly used for transmitting and receiving data over the web. Websites, web applications, and APIs use HTTP to communicate with clients, exchanging information and delivering content.
When to Choose SSH or HTTP
Choose SSH When:
– You need secure access to a remote server for administration, file management, and command execution.
– Security is a priority, as SSH ensures data confidentiality, integrity, and authentication.
Choose HTTP When:
– You are developing a website, web application, or API that relies on request-response communication between clients and servers.
– You need a protocol that supports caching and extensibility.
Conclusion
In conclusion, while both SSH and HTTP are protocols that allow communication between clients and servers over the internet, their differences in security, usage scenarios, and communication models make it crucial to choose the right one based on your specific requirements. As a programmer or server administrator, understanding these differences will enable you to make informed decisions and ensure that your connections are both secure and efficient. So next time you find yourself at the crossroads of SSH and HTTP, you’ll know exactly which path to take.
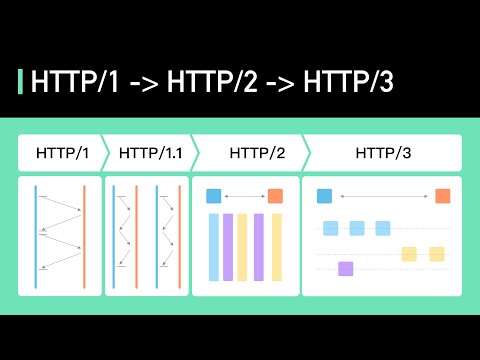
HTTP/1 to HTTP/2 to HTTP/3
How SSH Works
Difference between Web Server and Application Server! Apache Http Server ,Weblogic,Tomcat, Jboss
What distinguishes HTTP, HTTPS, SSL, and SSH from one another?
In the context of Secure Shell, it is crucial to understand the differences between HTTP, HTTPS, SSL, and SSH. These protocols play a significant role in secure communication over computer networks.
HTTP (Hypertext Transfer Protocol) is a fundamental protocol used for transmitting data, such as webpages, over the internet. However, HTTP does not provide any encryption or security measures to protect sensitive information during transmission.
HTTPS (Hypertext Transfer Protocol Secure) is an extension of HTTP that adds an extra layer of security. It uses SSL (Secure Sockets Layer), a cryptographic protocol, to encrypt data and ensure that it cannot be intercepted or tampered with during transmission. This makes HTTPS ideal for sensitive activities, such as online banking or e-commerce.
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols designed to provide secure communication over a computer network. SSL/TLS encrypts data, ensuring that it remains private and unaltered during transmission. These protocols are widely used to secure web traffic, email, and other sensitive information.
SSH (Secure Shell) is another cryptographic network protocol, but it is specifically designed for managing remote services and securely accessing remote servers. SSH provides a secure channel for authentication, encryption, and terminal access, making it a popular choice for administration tasks, file transfers, and remote command execution. SSH is often used to replace insecure protocols like Telnet and FTP.
To summarize, while HTTP and HTTPS are concerned with the secure transfer of web content, SSL/TLS provide encryption for various protocol communications, and SSH focuses on secure remote management and access to servers. These protocols are essential components in ensuring secure communication within modern computer networks.
Is it possible to use SSH over HTTP?
Yes, it is possible to use SSH over HTTP, but it requires a special setup since SSH typically communicates over a direct TCP connection. One common solution is to use an HTTP proxy server that supports the CONNECT method. This method forwards network traffic from the client to the target server via the proxy, allowing communication between the SSH client and server over an HTTP connection.
There are also tools like Shell-In-A-Box and WebSSH that enable running SSH sessions in a web browser, but they don’t provide a true SSH-over-HTTP experience as they use Websocket to bridge the connection between the browser and SSH server.
It’s important to note that using SSH over HTTP might be less secure than using it over a direct TCP connection, and network administrators may block CONNECT method on proxy servers to prevent potential security risks, thus making it unusable for SSH connections.
Rewrite the following question: Is SSH HTTP or TCP? Write only in English.
Regarding Secure Shell (SSH), can it be classified as either HTTP or TCP? Please provide answers exclusively in English and emphasize the most crucial aspects of the response using bold tags.
What is the purpose of utilizing SSH?
The purpose of utilizing SSH (Secure Shell) is to provide a secure method for accessing and managing remote systems over an unsecured network. SSH enables users to perform various tasks, such as file transfer, remote command execution, and remote system administration, in a more protected manner.
The most important reasons for using SSH include:
1. Encryption: SSH encrypts data transmitted between the client and the server, ensuring that sensitive information remains confidential and safe from unauthorized access or eavesdropping.
2. Authentication: SSH uses strong authentication mechanisms, like public key authentication, to confirm the identity of the parties involved in the connection. This prevents unauthorized users from gaining access to your system.
3. Integrity: SSH ensures the integrity of the transmitted data by generating a unique digital signature for each message. This helps detect tampering, corruption, or alteration of the data during transmission.
4. Port Forwarding and Tunneling: SSH allows users to securely forward network connections through an encrypted tunnel. This can be useful for bypassing firewalls or securing non-encrypted protocols.
In summary, the primary purpose of utilizing SSH is to safeguard data and communications between remote systems, providing a higher level of security and protection compared to other unsecured methods.
What are the key differences between SSH and HTTP protocols in terms of security and usage within {topic}?
In the context of secure shell, there are several key differences between SSH and HTTP protocols in terms of security and usage.
Firstly, SSH (Secure Shell) is primarily used for securely accessing and managing network devices, servers, and other systems remotely. SSH provides encrypted communication between the client and the server, ensuring that any sensitive data or information is protected from eavesdropping and tampering. In contrast, HTTP (Hypertext Transfer Protocol) is designed specifically for transferring data over the web, such as serving web pages from a server to a client’s browser.
Secondly, authentication methods differ between the two protocols. SSH typically uses public key authentication, which adds an additional layer of security, as it requires both a private and a public key for successful authentication. HTTP, on the other hand, relies on usernames and passwords, which can be more easily intercepted or guessed by attackers. Furthermore, SSH also supports multi-factor authentication for additional safety.
Another significant difference lies in encryption. As mentioned earlier, SSH encrypts all data transmitted over the connection. This ensures the confidentiality and integrity of any data and commands sent between the client and the server. In contrast, standard HTTP does not use encryption – all data is sent as plain text, making it vulnerable to interception by third parties. The secure version of HTTP, HTTPS, does provide encryption, but it is mainly focused on the confidentiality of data exchanged within the context of web applications.
Lastly, in terms of usage, SSH is commonly employed for remote administration, file transfers using SFTP or SCP, as well as setting up secure tunnels for other protocols like VNC or RDP. HTTP is primarily utilized for serving web pages and associated content such as images, stylesheets, and JavaScript files. It is important to use the appropriate protocol for their intended purposes to ensure optimal security and performance.
In summary, the key differences between SSH and HTTP protocols in terms of security and usage include their primary functions, authentication methods, encryption, and typical use cases. SSH provides a secure, encrypted connection for remote access and management, while HTTP is designed for transferring data over the web.
How do SSH and HTTP handle authentication and encryption differently when applied to {topic}?
In the context of secure shell, it is essential to understand how SSH and HTTP handle authentication and encryption differently when applied to a specific topic.
Firstly, SSH (Secure Shell) is a cryptographic network protocol primarily focused on providing secure access and communication over an unsecured network. It establishes an encrypted channel between a client and a remote server, enabling administrators to securely log in to a remote computer or perform file transfers.
On the other hand, HTTP (Hypertext Transfer Protocol) is an application-layer protocol used for transmitting hypermedia documents, such as HTML, over the internet. It operates on a request-response model between a client and server but does not inherently provide authentication and encryption.
Authentication:
– SSH employs public key cryptography to authenticate users and remote hosts. It uses a pair of private and public keys to establish trust and verify identity, ensuring that the client and server are who they claim to be.
– HTTP, by default, does not provide authentication. However, a few authentication methods, like Basic, Digest, and Bearer tokens are implemented on top of HTTP to provide user verification. These methods are less secure than SSH’s because credentials are often transmitted in plain text or using weak encryption.
Encryption:
– SSH uses strong symmetric encryption to protect data in transit. Every new session generates a unique session key, ensuring that even if an attacker intercepts the traffic, they cannot decrypt the data without the session key.
– HTTP transfers data in clear text, which makes it susceptible to eavesdropping and man-in-the-middle attacks. To overcome this vulnerability, HTTPS (HTTP Secure) was developed, which enforces the use of SSL/TLS (Secure Socket Layer / Transport Layer Security) protocols to encrypt the data transmitted between the client and server.
In summary, SSH provides built-in authentication and encryption mechanisms, making it a more secure choice for data transmission and remote access. HTTP, by default, lacks these features, but the HTTPS variant improves security by incorporating SSL/TLS encryption. When applying these protocols to a specific topic, it is vital to consider the inherent risks and choose the appropriate protocol based on the desired level of security.
In the context of {topic}, when should one choose to use SSH over HTTP, and what are the advantages and drawbacks of each protocol?
In the context of Secure Shell (SSH), when should one choose to use SSH over HTTP, and what are the advantages and drawbacks of each protocol?
SSH is a cryptographic network protocol mainly used for remote administration of servers and other devices, data transfer, and network-related services throughout a secure and encrypted connection. On the other hand, HTTP is a widely-used application-level protocol for transmitting hypertext information between servers and browsers, which was initially plain text but has evolved into using Transport Layer Security (TLS) encryption with HTTPS.
When to choose SSH over HTTP:
1. For secure remote access to servers or devices for administrative purposes.
2. When needing to establish a secure tunnel for transferring sensitive data between two points.
3. Performing version control system operations, such as Git repositories, securely and efficiently.
4. When executing remote commands or running scripts on a server or device.
Advantages of SSH:
1. Strong encryption: SSH provides end-to-end encryption for data transfer, ensuring the confidentiality and integrity of transmitted data.
2. Authentication: SSH uses public-key cryptography for user and host authentication, making it harder for intruders to gain unauthorized access.
3. Port forwarding and tunneling: SSH allows for secure forwarding of data across multiple services, creating encrypted tunnels for data transport.
Drawbacks of SSH:
1. Limited application scope: SSH is focused on providing secure remote access to servers and devices; it may not be suitable for web-related tasks or transferring data between clients and servers in web applications.
2. Complexity: Implementing and managing SSH can be complex, requiring expertise in cryptography, keys, certificates, and configurations.
When to use HTTP:
1. Hosting and developing web-based applications and websites.
2. API communication: Providing a standardized way for different software systems to communicate with each other in a stateless manner.
3. Fetching or submitting data to/from a server in a web application context.
Advantages of HTTP:
1. Ubiquity: HTTP is a fundamental protocol for web-based applications and services, ensuring compatibility across platforms and devices.
2. Simplicity: HTTP is relatively easy to implement, manage, and maintain when compared to SSH.
3. Statelessness: HTTP allows for independent requests and responses, making it easier to scale web applications without maintaining information about previous interactions.
Drawbacks of HTTP:
1. Lack of inherent security: HTTP requires additional measures, like HTTPS and TLS, to provide encryption and authentication for secure data transfer.
2. Performance: Stateless nature can lead to overhead in authenticating and establishing secure connections for every request-response cycle.
In summary, choose SSH over HTTP when you need secure remote access, encrypted data transfer, and remote command execution. Use HTTP for web-based applications, client-server communication in web context, and API development.
Can you provide specific examples of using SSH and HTTP for various tasks in {topic}, and explain their implications on performance and security?
In the context of Secure Shell (SSH), let’s explore various tasks involving both SSH and HTTP, along with their implications on performance and security.
1. Remote server management
SSH: With SSH, you can securely access and manage remote servers through an encrypted channel. For example, using the command `ssh user@remote_server`, you can log in to the remote server and execute commands.
HTTP: Although not designed for server management purposes, HTTP can be used to manage remote servers via web-based control panels like cPanel or Webmin. However, this approach is generally less secure than using SSH since the possibility of potential vulnerabilities in web applications may expose the server to attacks.
2. File transfer
SSH: Secure file transfers can be done using SCP (Secure Copy) or SFTP (SSH File Transfer Protocol). These protocols ensure data confidentiality, integrity, and authentication during transmission. For example, use the command `scp local_file user@remote_server:/path/to/destination` to transfer files securely.
HTTP: File transfer over HTTP is possible using methods like POST and PUT. However, these transfers lack built-in encryption (unless HTTPS is used), making them less secure than SCP or SFTP.
3. Tunneling and port forwarding
SSH: SSH can create secure tunnels between client and server, allowing you to forward traffic from one port to another securely. For instance, with the command `ssh -L local_port:remote_host:remote_port user@remote_server`, you can create a local-to-remote port forwarding tunnel.
HTTP: HTTP does not inherently support tunneling or port forwarding, making it unsuitable for cases where secure communication is required.
4. Version control access
SSH: Developers often use SSH to securely access version control systems like Git. With SSH keys, you can authenticate and establish secure connections to repositories without using passwords.
HTTP: Although HTTP(S) can be used for version control access, it may be less secure than SSH as it often requires password authentication, and the traffic is only encrypted when HTTPS is employed.
In conclusion, SSH provides a more secure and versatile solution for tasks like remote server management, file transfer, tunneling, and version control access. On the other hand, HTTP (and HTTPS) can serve as an alternative in specific scenarios, though they may not match the level of security and functionality provided by SSH.
How can one integrate both SSH and HTTP protocols into a single solution within {topic}, and what are the best practices for ensuring seamless functionality?
In the context of Secure Shell (SSH), integrating both SSH and HTTP protocols into a single solution can be achieved by utilizing SSH tunneling. This method allows for secure, encrypted communication over an otherwise unsecured network. The best practices for ensuring seamless functionality include proper configuration, access control, and regular maintenance.
1. Configuration: Configure the SSH server to listen on a specific port, typically the default TCP port 22. To enable HTTP traffic forwarding, create a local or dynamic SSH tunnel. This involves specifying the local port that will redirect to the remote server’s HTTP port. For example, using the command:
“`
ssh -L local_port:remote_server:remote_port user@remote_server
“`
This command creates a secure tunnel, forwarding the local port to the remote server’s HTTP port.
2. Access Control: Properly manage access control to ensure only authorized users can connect to the SSH server. Implement key authentication instead of password-based authentication, as it provides better security. To restrict access to the tunnel, use firewall rules and apply stringent policies on the SSH server.
3. Regular Maintenance: Regularly update your SSH server software and security patches to protect against known vulnerabilities. Monitor logs and usage patterns to detect any malicious activities or unauthorized access attempts. Establish a secure connection timeout and limit the number of simultaneous connections.
By following these best practices, integrating both SSH and HTTP protocols into a single solution within Secure Shell becomes more effective, resulting in seamless functionality and enhanced security.